Textpattern CMS support forum
You are not logged in. Register | Login | Help
- Topics: Active | Unanswered
Plugin supply chain security considerations
Yesterday I received a message from WordPress.org Plugin Directory stating that “We identified that some plugin authors were reusing passwords exposed in data breaches elsewhere. […] attackers used recycled passwords to add malicious code to a few plugins on the WordPress.org Plugin Directory.”
This supply chain security breach was discovered by WordFence1.
The attack vector was a very sophisticated, year-long trust attack on the sole maintainer of XZ Utils, a core component of a number of critical IT infrastructure components.
As one IT security professional I know told me, supply chain attacks are on the rise. This attack vector could apply to plugin authors as well as plugin installers.
Although we are not in a position to control a monopolistically large part of the web, which is run by partially inexperienced or technically agnostic site owners, I think it would be beneficial to be very aware of how the other forces work these days.
Personally, I was very surprised by the sophistication and effort that went into this attack.
1 www.wordfence.com/blog/2024/06/an-inside-look-at-the-malware-and-techniques-used-in-the-wordpress-org-supply-chain-attack/, www.wordfence.com/blog/2024/06/3-more-plugins-infected-in-wordpress-org-supply-chain-attack-due-to-compromised-developer-passwords/
Offline
Re: Plugin supply chain security considerations
An intriguing read. Thanks for raising it.
If there are libraries upon which we depend and pull in from Composer that get compromised, we could have a problem in Textpattern core too.
The smd plugin menagerie — for when you need one more gribble of power from Textpattern. Bleeding-edge code available on GitHub.
Hire Txp Builders – finely-crafted code, design and Txp
Offline
Re: Plugin supply chain security considerations
I have a background task of integrating VirusTotal into our Github CI builds so we have something in place when commits hit the pipes. I’ll push this up the priority queue for testing.
Offline
Re: Plugin supply chain security considerations
Pete, I’ve taken the liberty of throwing this issue to an infosec pro I know to see what sticks.
His response, roughly translated into a language I understand a little, was:
- VirusTotal uses signature matching AFAIK, which would probably be of little effectiveness given our threat model.
- Try SonarQube for source code analysis, including SAST for each commit/merge.
- Try DAST with e.g. OWASP ZAP on a freshly deployed demo installation each time for dynamic testing.
Ring any bells? Me neither ;) If they do, I can (step #1) relay any requests and (step #2) get out of the way if desired.
Offline
Re: Plugin supply chain security considerations
Thanks, Robert.
SonarQube and ZAP look interesting, I’ll investigate those.
I’ve got PHPStan on my list for static analysis, and a small heap of other bits & pieces after Textpattern 4.9.0 lands.
A spare week or two would be really very helpful, but I’ll find time as it appears!
Offline
Re: Plugin supply chain security considerations
Offline
Re: Plugin supply chain security considerations
agovella wrote #337369:
wait… what?
Is 4.9 close?
I’ve been using the dev versions for some time without any issues.
Yiannis
——————————
NeMe | hblack.art | EMAP | A Sea change | Toolkit of Care
I do my best editing after I click on the submit button.
Offline
Re: Plugin supply chain security considerations
agovella wrote #337369:
wait… what?
Is 4.9 close?
It’s been close for about 6 months 😳
Just waiting on one CSS fix on the Plugins panel to filter through. Or revert the code that needs it for now.
The smd plugin menagerie — for when you need one more gribble of power from Textpattern. Bleeding-edge code available on GitHub.
Hire Txp Builders – finely-crafted code, design and Txp
Offline
Re: Plugin supply chain security considerations
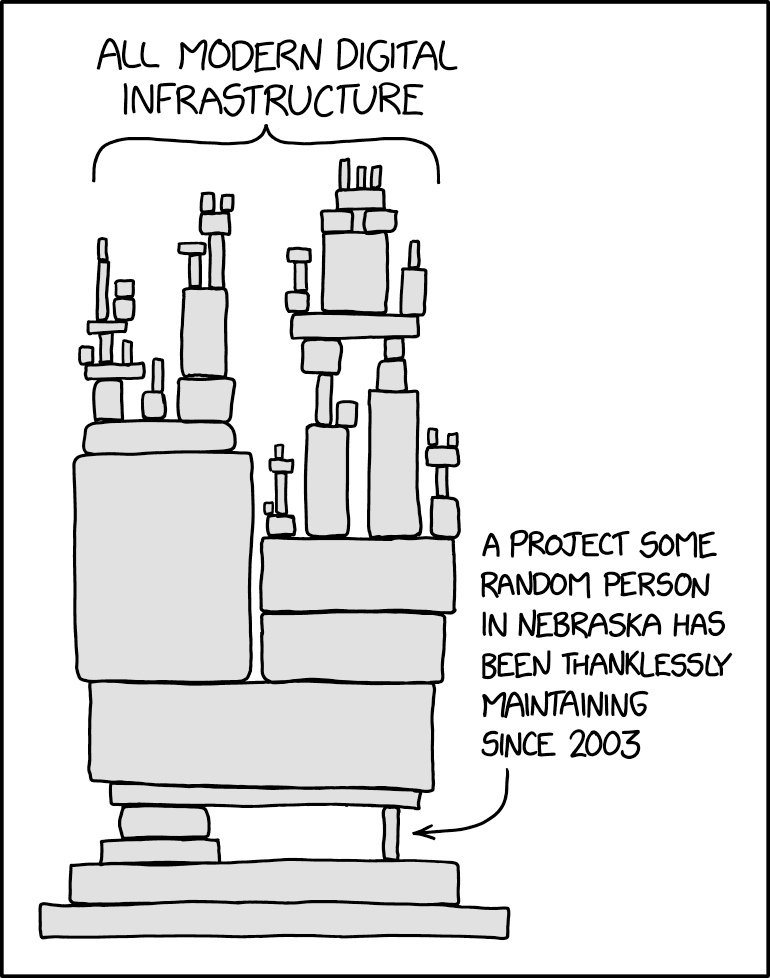
Related article:
Having seen the XZ sabotage, some of them are now taking a deep breath and thinking, “OK, I guess I won’t be retiring anytime soon then…” Others are wistfully thinking, “I’d happily do this for the next 30 years, but I have a mortgage to pay.” […]
The best we can hope for, of course, is to convince companies, institutions, and governments that it would be a really good idea to cut monthly checks for those people who maintain the software that these organizations absolutely depend upon.
Offline
#10 2024-07-10 08:02:15
- Algaris
- Member
- From: England
- Registered: 2006-01-27
- Posts: 604
Re: Plugin supply chain security considerations
That was an interesting read and I agree 100% with the articles author. We had a lucky escape. Who’s to say next time we will be as lucky? The people who maintain these systems we rely should be recognised and compensated for their work.
Offline